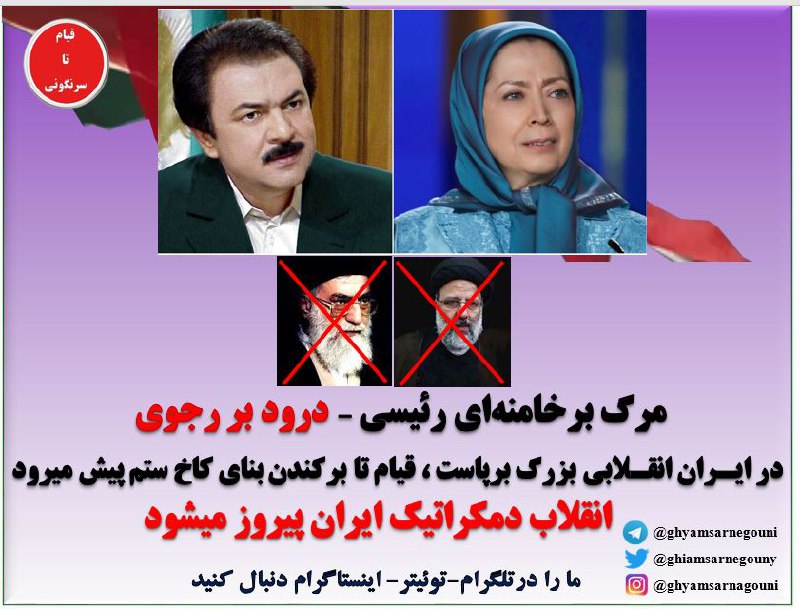
May 29, 2023: A group of dissidents in Iran, known as “GhyamSarnegouni”, has claimed responsibility for their actions in gaining control of and altering multiple websites affiliated with the Iranian presidency.
On Monday, May 29, these well-protected sites were breached, with the dissidents replacing images of Supreme Leader Ali Khamenei and President Ebrahim Raisi with those of Massoud Rajavi, the Leader of the Iranian Resistance, and Maryam Rajavi, the President-elect of the opposition coalition National Council of Resistance of Iran (NCRI). Some websites displayed crossed-out images of Khamenei and Raisi.
The dissident group, previously involved in disrupting websites associated with the regime’s Foreign Ministry, has once again caused a stir. Just this month, “GhyamSarnegouni” claimed to have acquired over 50 terabytes of data from the Foreign Ministry’s servers.
In recent times, the regime has become a target of various hacking incidents that have exposed sensitive information, including attacks on its nuclear program, state television broadcasts, and government surveillance cameras.
The dissident group has shared detailed accounts of their recent disruption and alteration of Iranian presidency-linked websites. The following are the key elements they have revealed:
- Images of Iranian Resistance leaders and anti-regime slogans were sent to journalists and media outlets from the regime’s presidency main email account.
- The group gained control of 120 servers within the presidency’s internal network, including central databases.
- They obtained control over the government’s server management network and server controllers.
They gained control over the presidency’s network of technical administrators.
- They gained control over the “Users Internal Network” and accessed more than 1,300 computers within the presidency’s internal network.
- They obtained security footage from the presidency’s communication network hardware.
- They obtained access to systems handling classified internal communications associated with the presidency and the government.
- They extracted and decrypted classified and encrypted messages from recent years.
- They gained access to tens of thousands of classified, top secret, and secret documents related to the presidency, including the appointment of Ali Akbar Ahmadian as the new Secretary of the regime’s Supreme National Security Council.
- They gained access to the presidency’s websites and numerous internal applications.
- They gained access to other classified documents, such as the architectural design of Raisi’s office and sleeping quarters, the fiber-optic cable network connecting the presidency to Khamenei’s headquarters, and various entities within the mullahs’ regime, including the government cabinet, judiciary, Interior Ministry, Intelligence Ministry, Foreign Ministry, the IRGC paramilitary Basij Force, the Majlis (parliament), state TV and radio facilities, Tehran’s airports, and more.
- They obtained 19 pages of technical infrastructure details about the presidency’s computer network, including the fiber-optic network map and buildings’ patch panel, as well as 21 pages on the presidency’s technical network, including IP addresses, 104 pages of telephone numbers, internal phone systems, and direct lines connecting all rooms within the presidency building.
- They obtained classified documents outlining Raisi’s planned trips abroad for 2023, including destinations such as Iraq, Syria, Pakistan, Indonesia, Kyrgyzstan, Oman, Uganda, Zimbabwe, Kenya, Venezuela, Cuba, Nicaragua, Uzbekistan, South Africa, India, the Shanghai summit, the Caspian Sea summit, Tajikistan, Kazakhstan, the UN General Assembly in New York, Uzbekistan, and Gambia.
They obtained the names of the 25-member security team of Iranian regime First Vice President Mohammad Mokhber.
- They accessed top secret letters from the IRGC command in Tehran, which revealed at least five meetings.



